Security incidents can have a drastic impact on companies, causing severe organisational and financial damage. Therefore, when it comes to safeguarding sensitive data and protecting against cyber threats, understanding how to manage information security incidents is paramount. Cyber security incident response encompasses a range of strategies and protocols aimed at detecting, mitigating, and recovering from security breaches effectively. By implementing robust incident response plans, organisations can minimize the impact of security incidents and ensure business continuity.
Enhancing Information Security Through Human-Centric Approaches
The causes of security incidents are, to a large extent, human errors. Implementing sound procedures and processes is only possible if a company has a very good security and open error culture. Fundamentally, correct handling can be divided into 3 areas:
- Monitoring of information security incidents
- Collecting evidence
- Reaction to information security incidents
The ISO 27000 standards provide excellent guidelines for handling information security incidents correctly. Such a framework should be used depending on the company’s size.
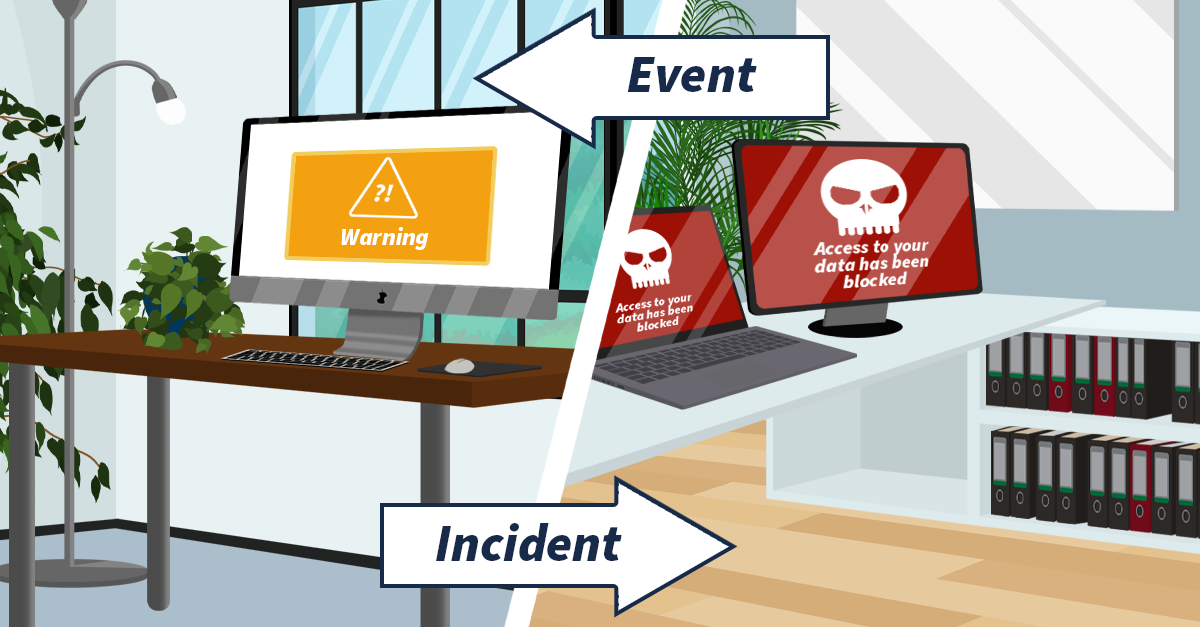
Difference Between Security Event and Security Incident
An information security event is always when an event has been identified in a system, service or network that indicates a possible breach of security guidelines or a previously unknown circumstance that could be security-relevant. Therefore, in the case of an event, it is not yet possible to report on the effects or the exact hazard situation. On the other hand, a security incident is an event that has occurred and is most likely to have jeopardised business operations and information security. Thus, one of the main components of proper handling is the correct monitoring and analysis of incidents, as the following chart shows:
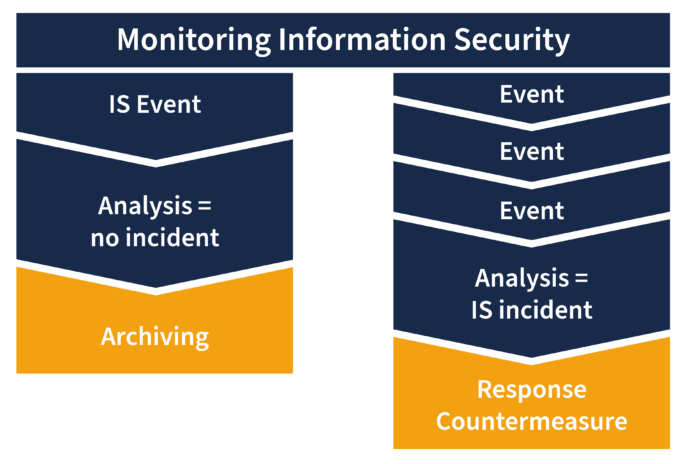
How to Reduce Information Security Incidents
The security culture significantly influences the number and impact of information security incidents within a company. There should be a clear structure in the company on how to proceed, which every person involved has internalised. This creates security. If the procedure is clear, this results in a lower error rate, and tasks and communication channels can be processed more efficiently. Also, a clear separation between events and incidents is necessary to enable meaningful prioritisation. Furthermore, errors should be allowed to be openly communicated so that events are not concealed and so that the time factor can be used for the subsequent reactions and countermeasures.
Advanced Persistent Threats (APTs) – Targeted Cyberattacks
APTs are targeted attacks on selected individuals, companies or institutions. In the process, permanent access is gained to a network, aiming to spread to other IT systems. The profile of the attackers is characterised by a high level of motivation and very high use of resources. Criminal organisations are usually behind these attacks, which have serious consequences.
In order to clean up the effects of such incidents in the best possible way, a pre-prepared structure and flow charts are required. First, affected systems should be shut down or isolated to reduce the spread. Then, nothing should be rushed, and the affected IT environment can be cleaned up according to plan. Once all steps have been completed, the environment can be returned to productive status after clean-up.
The Importance of IT Forensics for Security Incidents
Let’s assume our workstation has been compromised by an attacker and malicious code has been executed to infect other IT systems. Now, before further systems have been infiltrated, the compromised system can be identified and shut down. However, it is also important to carry out a forensic analysis of the system in order to be prepared for further similar incidents and to contain the effects of the incident. External experts can be consulted, or internal teams can be established.
When forensic teams handle security incidents, the first focus is on locking the attacker out of the system. This is followed by an analysis and clarification of the most important questions:
- What circumstances allowed the system to be compromised?
- Which security holes were exploited?
- When did the attack happen, and how long has it been going on?
Once all questions have been clarified, measures can be implemented and the gateways closed.
Incident Response Management for Remote Work
Due to the increasing number of remote workers and the rapid change caused by the Corona pandemic, there has often been uncertainty among many employees. As explained in previous sections, insecurity is one of the biggest factors for information security incidents and favours serious repercussions. For this reason, monitoring measures must be further expanded, especially in remote workspaces, and access to company networks must be clearly assignable. This is the only way to compensate for the exponentially increased attack surface. An important point is a very well structured and easily accessible reporting process for information security incidents by employees. Reporting chains and contact persons should be communicated regularly. Furthermore, awareness measures are necessary to make the threats constantly present and to train procedures. Only then can the error rate be reduced and self-confidence in dealing with information security incidents and events be created.
Proactive Cyber Security Incident Response: Safeguarding Your Organisation’s Digital Assets
Security incidents pose significant risks to organisations, ranging from financial losses to reputational damage. However, with the right approach to cyber security incident response, these risks can be mitigated effectively. Explore MetaCompliance’s comprehensive cyber security awareness training for employees to empower your workforce with the knowledge and skills needed to prevent, detect, and respond to security threats proactively. Invest in proactive measures today to safeguard your organisation’s digital assets tomorrow.