Den konstante strøm af højt profilerede databrud har gjort os meget opmærksomme på, hvor værdifulde vores data er blevet, og hvilken skade det kan medføre, hvis de falder i de forkerte hænder.
Der er mange grunde til, at hackere ønsker at få fat i vores følsomme data, men oftest handler det om penge. Vores data kan bruges til at begå identitetssvindel, handles på hackerfora eller sælges videre til den højestbydende på det mørke net.
Dark Web er den perfekte platform for hackere til at handle med deres stjålne data uden frygt for repressalier. Der er kun adgang til det ved hjælp af specialiseret software, og alle websteder, der er hostet på dark web, er krypterede og kan ikke findes ved hjælp af traditionelle søgemaskiner eller browsere.
De fleste websteder skjuler deres identitet ved hjælp af et Tor-krypteringsværktøj. Tor leder effektivt internettrafikken gennem en række proxyservere, der drives af tusindvis af frivillige rundt om i verden. Det gør det ekstremt svært for nogen at identificere brugeren, dennes placering eller browsingvaner.
Den anonymitet, som dette giver, gør det til en stor attraktion for de brugere, der ønsker at deltage i ulovlige eller svigagtige aktiviteter såsom narkohandel, våbensmugling, prostitution og forfalskede varer, for ikke at nævne det enorme marked for stjålne legitimationsoplysninger og personlige data.
En nylig undersøgelse fra Digital Shadows har vist, at der cirkulerer op til 15 milliarder stjålne legitimationsoplysninger på det mørke net, hvilket giver os et indtryk af dette markeds enorme omfang.
Dette enorme underjordiske kriminelle netværk fungerer 24 timer i døgnet, 7 dage om ugen og giver hackere et ideelt sted at sælge og tjene penge på deres stjålne data.
Men hvor meget er vores data egentlig værd?
Overraskende nok ikke så meget, som du tror! Der er flere faktorer, der påvirker prisen på dine data online, men det hele afhænger af udbud og efterspørgsel. Hvis der er et lavt udbud af særligt værdifulde oplysninger, vil disse naturligvis blive mere attraktive for kriminelle.
Der er også forskellige priser på forskellige typer data. En af de hotteste varer, der kan købes i dette undergrundsnetværk, er stjålne personhenførbare oplysninger (PII). Det er data, der kan bruges til at identificere eller lokalisere en person, og som typisk omfatter brugernavne, adgangskoder og kontaktoplysninger.
Personlige sundhedsoplysninger (PHI) er også blevet mere og mere værdifulde og kan sælges for mellem 100 og 350 dollars. Disse data kan omfatte fødselsdatoer, navne på slægtninge, medicinske procedurer, testresultater og i nogle tilfælde finansielle oplysninger og straffeattester.
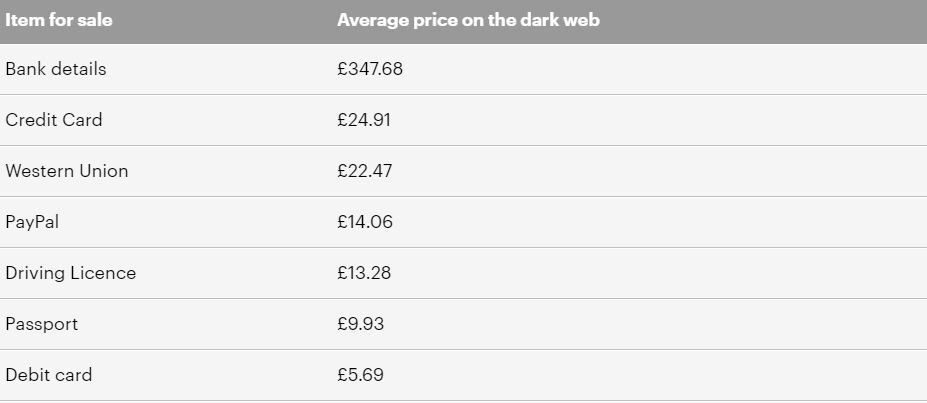
Kreditkortoplysninger er et af de mest handlede datasæt på det mørke net og sælges for mellem 5 og 30 pund pr. kort.
En nylig rapport fra Virtual Private Network (VPN) sammenligningstjenesten Top10VPN.com fandt ud af, at loginoplysninger til sociale medier kan købes for så lidt som 1 pund, mens et af de mest eftertragtede datasæt omfatter hackede bankkontodetaljer, som kan købes for omkring 347 pund.
En af hovedårsagerne til, at vores data handles til så lave priser, er, at hackere så let kan få fat i dem. Dette er til dels drevet af den enorme stigning i antallet af databrud og de milliarder af fortrolige oplysninger, der udsættes hvert år.
Det er interessant at bemærke, at efter at British Airways blev krænket i 2018, blev BA-kontodata oversvømmet på det mørke net og kunne købes for £31.94, hvilket er en prisstigning på 375 % i forhold til året før.
Det er tydeligvis et lukrativt marked, og så længe dette travle undergrundsnetværk fortsætter med at blomstre, vil cyberangreb fortsat være en konstant trussel mod enkeltpersoner og virksomheder i hele verden. Heldigvis er der en række skridt, som vi kan tage for at beskytte vores data online:
Sådan beskytter du dine data online
- Opret stærke og unikke adgangskoder
En stærk adgangskode bør være mellem 10-15 tegn lang, bestå af store og små bogstaver og indeholde tal eller symboler. For at opnå ekstra sikkerhed kan der oprettes en passphrase, som er en adgangskode, der består af en sætning eller en kombination af ord. Det første bogstav i hvert ord danner grundlaget for din adgangskode, og bogstaverne kan erstattes med tal og symboler for at gøre den endnu mere sikker.
- Klik aldrig på mistænkelige links
Phishing-svindel er omhyggeligt udformet for at narre dig til at indtaste fortrolige oplysninger som f.eks. et kontonummer, en adgangskode eller fødselsdato ved at klikke på et link. Beskeden kan også indeholde en vedhæftet fil, som, når den åbnes, direkte inficerer din computer med malware. Røde flag omfatter ofte en forkert URL-adresse, dårlig stavning og grammatik, anmodninger om følsomme oplysninger, uventet korrespondance eller brug af truende eller presserende sprogbrug.
- Vær forsigtig med, hvad du lægger ud på nettet
Hvis du vil mindske risikoen for at blive hacket, skal du tænke mere grundigt over, hvad du lægger ud på nettet. Udnyt de forbedrede muligheder for beskyttelse af personlige oplysninger, begræns adgangen til alle, du ikke kender, og opret stærke adgangskoder til dine konti på de sociale medier.
- Installer antivirus-software
Anti-virus-software registrerer trusler på din computer og forhindrer uautoriserede brugere i at få adgang. Software bør også opdateres regelmæssigt for at forhindre hackere i at få adgang til din computer via sårbarheder i ældre og forældede programmer. Regelmæssige softwareopdateringer sikrer, at du har de mest opdaterede versioner, som producenten har udgivet, og reducerer dermed risikoen for angreb.
- Undgå at bruge offentligt Wi-Fi
Offentligt Wi-Fi kræver ingen godkendelse for at etablere en netværksforbindelse, hvilket giver direkte adgang til usikrede enheder på det samme ukrypterede netværk. En VPN kan bruges til at kryptere din internetforbindelse, hvilket gør den sikker og beskytter dit privatliv. Andre sikkerhedsforanstaltninger omfatter bl.a. at slå deling fra, holde sig til sikre websteder og slukke for Wi-Fi, når det ikke er i brug.




