Hvad er "Hash Functions"? Hash-funktioner spiller en afgørende rolle i password-sikkerhed for sikre webtjenester. Disse tjenester gemmer aldrig din faktiske adgangskode, men gemmer i stedet en hash-version af den. Hash-funktioner er algoritmer, der konverterer inputdata (som en adgangskode) til en tegnstreng af fast størrelse. Denne proces er irreversibel, hvilket betyder, at det er næsten umuligt at udlede det oprindelige input fra hashen. Når du logger ind, hasher tjenesten den adgangskode, du giver, og sammenligner den med den gemte hash. På den måde kan hackere ikke få adgang til adgangskoder i klartekst, selv hvis der sker et databrud, hvilket forbedrer den overordnede sikkerhed.
En usofistikeret login-procedure
Lad os først se på, hvordan en usofistikeret login-procedure ville se ud. Vi logger ind på en webtjeneste på den sædvanlige måde med et kontonavn og en adgangskode:
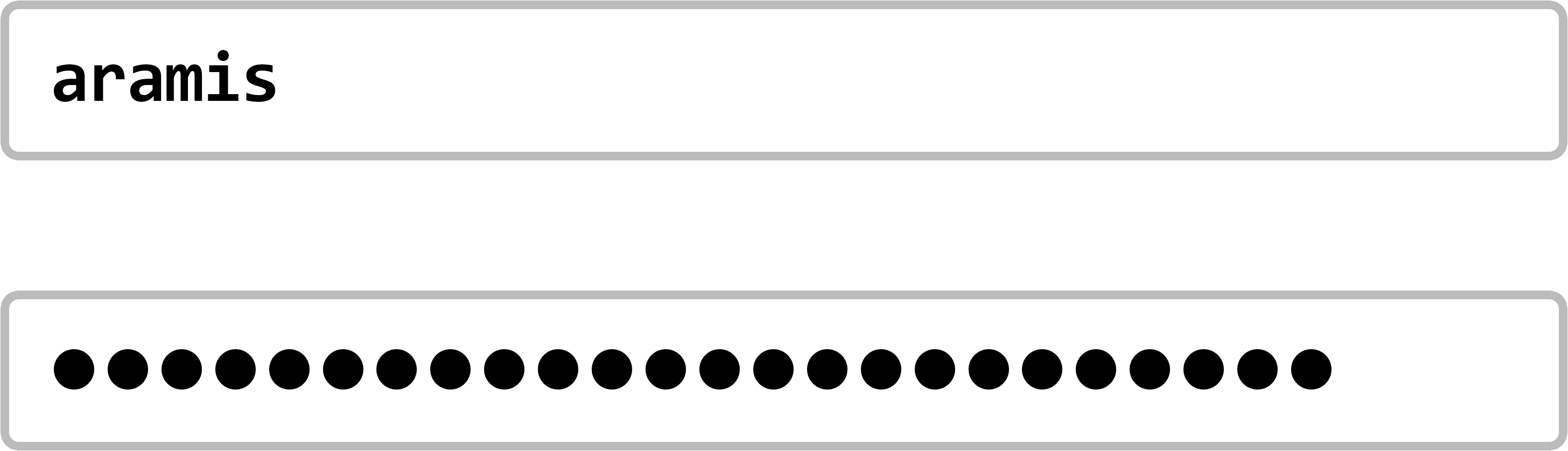
Vores usofistikerede webservice har en tabel i sin database med alle kontonavne og deres tilhørende adgangskoder:

Webservicen slår først kontonavnet fra den udfyldte login-formular op i sin database. Hvis navnet findes i databasen, sammenligner tjenesten også adgangskoden fra login-formularen med den tilhørende adgangskode i databasen. Hvis adgangskoderne matcher, udføres registreringen. Ellers bliver registreringen afvist. Ved første øjekast er dette en sikker login-procedure. Kun dem, der er i besiddelse af et gyldigt kontonavn og kender den tilhørende adgangskode, kan få adgang til den tilsvarende konto. Alle andre bliver nægtet adgang. Så langt, så godt! Men hvad er det lige, der er så usofistikeret ved denne procedure?
Problemet er, at adgangskoderne er gemt i en database. Det betyder, at de potentielt er kendt af alle, der har adgang til databasen, herunder webserviceoperatørerne og deres medarbejdere. Desuden er det nu almindelig praksis for mange virksomheder at outsource den faktiske drift af de webtjenester, de tilbyder, til amerikanske cloud computing-udbydere som Amazon Web Services eller Google Cloud. Derfor kan vi antage, at operatørerne og medarbejderne hos disse cloud computing-udbydere i princippet også har adgang til databasen og dermed til vores password. Derudover kan kriminelle selvfølgelig også få uautoriseret adgang til dataene i databasen.
Desuden er det ingen hemmelighed, at de fleste brugere af webtjenester genbruger det samme password til flere tjenester. Derfor vil den, der har fået fat i adgangskoden til en målgruppes Facebook/Twitter-konto eller online-rejsebureau, med lidt held også have adgangskoden til deres e-mail, netbank, personlige kalender, en datingplatform og intranettet i den virksomhed, hvor målgruppen arbejder. Det økonomiske incitament til at stjæle adgangskoder fra en hvilken som helst webtjenestes database er tilsvarende højt, selv hvis denne webtjeneste ikke selv er et lukrativt mål! Spørgsmålet er: Hvordan løser vi dette problem?
En mere sofistikeret login-procedure
Lad os huske tilbage: Webtjenesten beskrevet ovenfor har en tabel i sin database med alle kontonavne og de tilhørende adgangskoder:

Vi tilpasser denne tabel på følgende måde. I stedet for at gemme adgangskoderne anvender vi en kryptografisk hashfunktion efter eget valg på adgangskoderne:
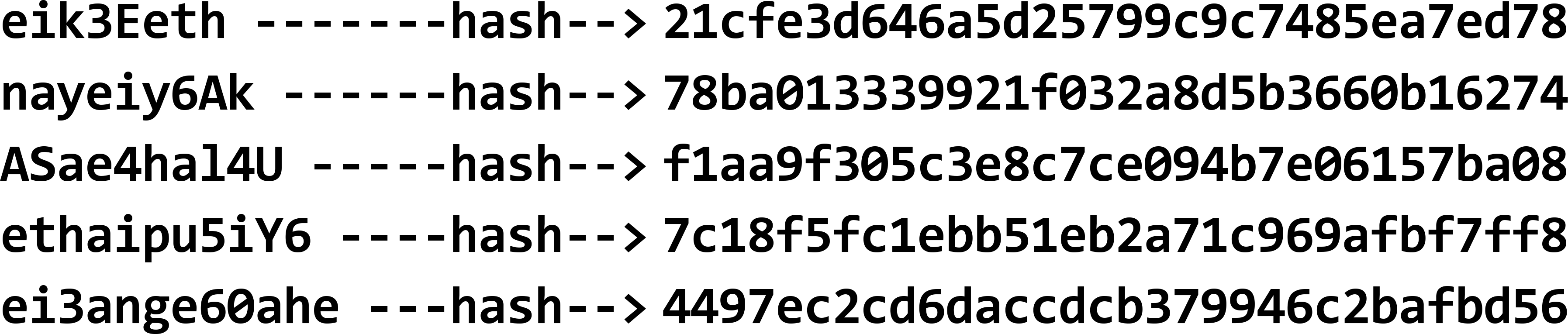
Derefter gemmer vi de resulterende hash-værdier i databasen i stedet for adgangskoderne:

Det ændrer kun login-proceduren en smule. Vi logger stadig ind på den sædvanlige måde med et kontonavn og en adgangskode:

Webtjenesten slår først kontonavnet fra den udfyldte loginformular op i sin database igen. Men i det næste trin er den nye procedure anderledes. Hvis navnet findes i databasen, anvendes hash-funktionen på adgangskoden fra login-skærmen. Først derefter sammenlignes den resulterende hashværdi med den tilsvarende hashværdi i databasen. Igen sammenlignes adgangskoderne ikke længere med hinanden, men kun med deres hash-værdier. Hvis hashværdierne stemmer overens, gennemføres login. Ellers nægtes login.
Bortset fra brugen af hash-funktionen er der ikke ændret noget i login-proceduren. Ud fra egenskaberne ved kryptografiske hashfunktioner følger det, at sammenligning af hashværdierne er lige så god som direkte sammenligning af adgangskoderne. Men nu er selve adgangskoderne ikke længere gemt i webtjenestens database. Enhver, der får adgang til databasen - autoriseret eller uautoriseret - har ikke længere adgang til adgangskoderne, men kun til deres hash-værdier. Det ovenfor beskrevne økonomiske incitament til at stjæle adgangskoder fra en webtjenestes database er dermed elimineret, fordi adgangskoderne nu ikke længere er indeholdt i databasen.
Sådan fungerer hash-funktioner i praksis
Vi håber, at vi bedre har kunnet forklare, hvordan det er muligt, og hvorfor det er almindelig praksis, at sikre webtjenester ikke engang kender de adgangskoder, vi bruger, når vi logger ind. I praksis øges sikkerheden i denne procedure yderligere ved at generere hashværdierne med en specialiseret kryptografisk hashfunktion (bcrypt) og desuden forbinde dem med en hemmelig tegnstreng (salt), der dækker hele databasen, før hashfunktionen anvendes.
Hvis du har glemt din adgangskode til en webtjeneste, kan du anmode om en nulstilling af adgangskoden fra de fleste webtjenester. Du vil så modtage en e-mail med et link, der fører dig til en formular, hvor du kan angive et nyt kodeord. Vi ved nu, hvorfor dette håndteres så akavet: webtjenesten kender ikke din gamle adgangskode. Desværre er det ikke alle virksomheder, der følger denne etablerede sikkerhedspraksis endnu. Hvis du via e-mail eller i en telefonsamtale med et supportteam fortæller, at du har glemt din adgangskode, og du så rent faktisk får oplyst din adgangskode, kan du konkludere, at virksomheden ikke overholder moderne standarder for informationssikkerhed. I hvert fald bør du sørge for, at du ikke bruger dette password i nogen anden sammenhæng. Hvis du konsekvent vil bruge et separat password til hver webtjeneste, bør du bruge en password manager. Så behøver du ikke længere at huske en masse individuelle adgangskoder og har den ekstra bonus, at du i stedet kan oprette tilfældige adgangskoder af høj kvalitet. Der findes browser-plug-ins til populære password managers, som endda udfylder login-skærmene til dine webtjenester for dig. Sjældent har bekvemmelighed og sikkerhed mødtes så smukt.
Integrering af password-sikkerhed og hash-funktioner i din personlige cybersikkerhedstræning
Konklusionen er, at hashfunktioner spiller en afgørende rolle for at beskytte passwords mod cyberangreb. Men deres effektivitet afhænger i høj grad af, hvor godt folk forstår og håndterer deres passwords. Det er her, cybersikkerhedstræning kommer ind i billedet. Ved at lære folk at lave stærke passwords og være opmærksomme på onlinetrusler kan vi alle være med til at beskytte vores personlige oplysninger. Husk, at det er en holdindsats at være sikker på nettet, og lidt knowhow rækker langt, når vi skal beskytte os selv i den digitale verden.