It’s late one Friday evening in the office when a message pops into your inbox from the CEO titled ‘Urgent transfer needed ASAP!’ What do you do?
This is a scenario too many people are becoming increasingly familiar with in the modern digital world. Unfortunately, the bite of phishing attacks are being felt throughout the UK and globally with 2016 witnessing a massive 65% increase. This leaves many organisations facing the mounting pressure to properly protect and educate their employees regarding these threats. So, what comprises a Phishing email? Below are some tips written from the perspective of a hacker ‘MataHacky’s Guide’ on how to spot the Phish and bite back!
#1 It’s ok to keep it generalised..but if you’re a real pro Spear Phish!

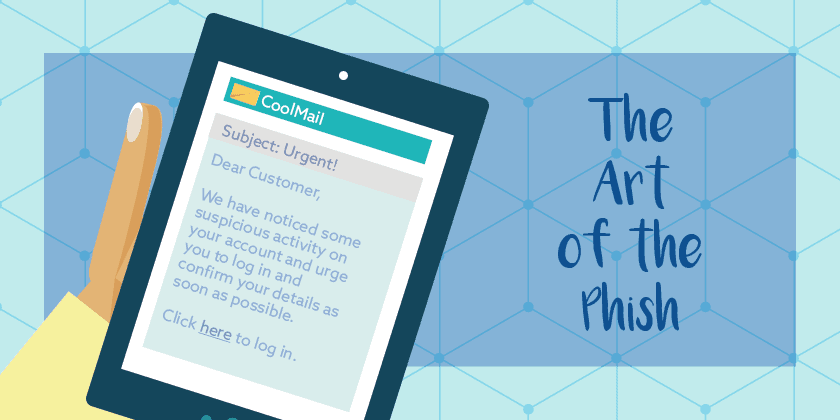
When starting off and targeting multiple people in one go, it’s ok to keep the naming general as we’re just looking for one sucker to bite. For example, ‘Dear Customer’ is enough to open with and will often be overlooked by an unsuspecting fool on the move with their busy lives. Many of them won’t even question that the email isn’t personalised and that you don’t address them by name. It’s important to note though that as awareness increases, more and more people will start to view this generalisation as a threat detector. This leads us to where the real money lies and the game changes pace- spear phishing! Basically, you’re looking to research your target, find out their name, workplace and even their boss’s name to create a super convincing personalised phish!
#2 Create a Sense of Urgency!

This is the key. You must instil fear in the audience. Without this they may look more closely at the other flaws in your email such as spelling mistakes and grow cautious. Like a horse out of the trap you have to get in there right away. Start with the email subject ‘Urgent- suspicious activity on your X account’ is usually a great way to open and get their attention. Remember to maintain this level of urgency throughout your email and you’re on to a winner. Panic is the key to a good phish. Think of what is most precious, such as details that will cause financial wreckage or reputational embarrassment, put it in a situation of jeopardy and you’re bound to get a bite.
#3 Watch out for your spelling and grammar

It is true that if you nail the other points I’ve listed that you can get away with the odd spelling mistake or grammatical error…however you do need to keep an eye on the amount of spelling mistakes in your text. One or two will probably go unnoticed but the super keen phish spotter will not be fooled so try to brush up on these as best as possible. After all any truly professional corporate company will not have spelling mistakes in the emails they send out to their customers.
On the other hand, spelling mistakes will help you create the perfect sucker list. I mean, if they fall for a phishing email full of spelling mistakes, what else could they fall for? You could even share these suckers contact details with your hacker friends so they can target them as well!
#4 Create a really convincing spoof email address and links!

To ensure that those fools will take the bait and click on the link you provide you must make sure the email address you are operating from looks legit. Just one character off from the real deal will usually be enough to fool them into clicking the link, again people’s attention to detail is often lacking so if they see an email come in from ‘[email protected]’ many will overlook these little mistakes. Apply the same idea to your links too! Make them look as real as possible and you can get away with just a little character here or there missing or added in. Spoofing is an art so if you want to be a master, you better get practicing!
Remember that 91% of corporate phishing attacks contain display name spoofs, 30% get opened and 12% of the suckers will click on the link or attachment so you’re chances of making a quick buck look good if you stick to my rules. Good Luck!
The average employee faces at least one risky email per day with email forecast to remain the primary targeting method for most attacks well through to 2020. In the past two years, fraudulent links sent to business email accounts have cost companies over two billion dollars with 30% of customers taking their business elsewhere following a breach.
Can you afford for your organisation or even your personal account to suffer at the hands of one of these attacks? If the answer is no, then you may be interested in our Essential Phishing Awareness eLearning course which covers how to correctly identify a phish and what to do when you spot one. This can also be complemented with our phishing simulation software ‘MetaPhish’ to help increase your employees’ sensitivity to fraudulent emails.
The biggest cyber security risk your company faces daily is employee complacency and now is the right time to turn this around. Talk to us today for more information on how you could save your organisation from a phishing attack.