El phishing, en todas sus formas, desde los correos electrónicos maliciosos hasta el SMShing (phishing de texto), pasando por el phishing de publicaciones sociales o el Vishing (phishing de llamadas telefónicas), forma ya parte de la vida cotidiana de una organización.
Sin embargo, los correos electrónicos de suplantación de identidad son, con diferencia, la forma más común de phishing.
¿Qué son los correos electrónicos de phishing?
Los correos electrónicos de phishing son mensajes fraudulentos enviados por ciberdelincuentes que se hacen pasar por entidades legítimas, con el objetivo de engañar a los destinatarios para que divulguen información confidencial o realicen acciones perjudiciales, como hacer clic en enlaces maliciosos o descargar programas maliciosos.
Según elinforme de Cisco "2021 Cybersecurity Threat Trends Report", alrededor del 90% de las violaciones de datos comienzan con correos electrónicos de phishing. Y lo que es más preocupante, el informe sugiere que en el 86% de las organizaciones, al menos una persona hará clic en un enlace de phishing. Pero, por supuesto, solo hace falta un clic para infectarse con ransomware o la exposición de datos sensibles, etc.
Comprender las tácticas utilizadas en algunas de las formas más comunes de ataques de phishing por correo electrónico y cómo pueden evitarlas los empleados ayuda a reducir el riesgo cibernético. He aquí cinco ejemplos de correos electrónicos de phishing y cómo evitar que los empleados corran riesgos.
La estafa de las facturas falsas
La estafa de las facturas falsas es una de las favoritas de los phishers. Los estafadores envían correos electrónicos con facturas falsas, con la esperanza de sorprender a un empleado desprevenido. Por desgracia, si se paga la factura falsa o se hace una consulta sobre la misma al estafador, es probable que se roben dinero o datos personales.
El tipo de factura incluida en los correos electrónicos de phishing varía, pero algunos ejemplos son los siguientes:
Facturación de productos de seguridad como antivirus
- Facturas vencidas de proveedores falsos
- Correos electrónicos de vencimiento de pago de dominio advirtiendo que si no actúa, su sitio web y correos electrónicos no estarán disponibles
- Facturas de fundaciones y organizaciones benéficas, a menudo ofreciendo un anuncio o un artículo en una publicación benéfica.
- Business Email Compromise (BEC) es una forma muy sofisticada y selectiva de estafa con facturas falsas.
Cómo evitar estafas con facturas falsas
Las estafas con facturas pueden ser muy sofisticadas, y los estafadores se dirigen a personas concretas, como los empleados de contabilidad o los directores financieros. Los correos electrónicos parecen auténticos y a menudo incluyen un mensaje urgente del tipo "pague ahora o sufra las consecuencias".
Utilice el phishing simulado que proporciona formación basada en roles para dirigirse a los tipos de usuarios con mayor riesgo de sufrir estafas de facturas falsas. Los simuladores de phishing basados en roles le permitirán adaptar sus campañas de phishing simulado para reflejar los desafíos de la vida real a los que se enfrentan departamentos y personal específicos.
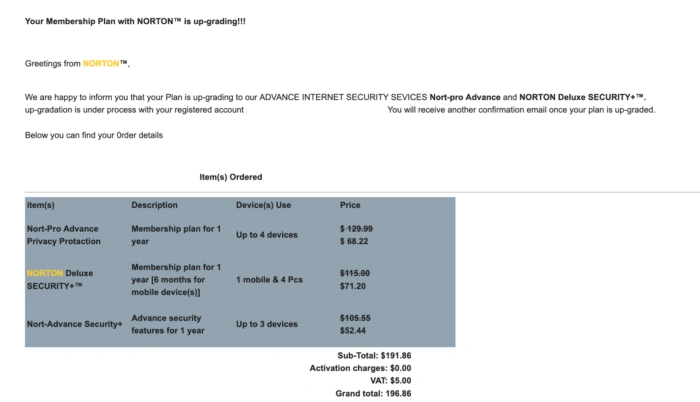
Correos electrónicos falsos de asistencia técnica
Crear una sensación de urgencia y de cumplimiento son dos de las técnicas de manipulación utilizadas por los estafadores para engañar a los empleados y conseguir que hagan clic en enlaces maliciosos o descarguen archivos adjuntos infectados. Un ejemplo de estas manipulaciones del comportamiento se observa en los correos electrónicos de phishing que simulan proceder del servicio de asistencia técnica.
En el siguiente ejemplo, se puede ver cómo se insta al personal a cambiar a un nuevo portal web para acceder a información importante personal y de la empresa, incluidas sus nóminas. El correo electrónico recuerda al personal que solo dispone de 24 horas para cumplir la normativa.
El correo electrónico contiene un enlace a un sitio web malicioso. Si el empleado hace clic en este enlace y navega hasta el sitio web, se le pedirá que introduzca sus credenciales de inicio de sesión y sus datos personales. Si lo hace, estos datos serán robados y los estafadores utilizarán las credenciales de inicio de sesión para acceder al portal real.
Cómo evitar falsos correos electrónicos de asistencia técnica
Todo el personal corre el riesgo de sufrir este tipo de correo electrónico de phishing especulativo general. La formación general sobre concienciación en materia de seguridad debe utilizarse para educar a todos los empleados, en todos los departamentos, sobre cómo estar seguros en línea.
La educación sobre cómo los ciberdelincuentes manipulan el comportamiento humano es crucial para formar a los empleados sobre las tácticas utilizadas por los estafadores a la hora de crear correos electrónicos de phishing. Los programas eficaces de formación para la concienciación sobre la seguridad utilizarán el aprendizaje en el punto de necesidad que aprovecha las oportunidades para reeducar los comportamientos deficientes en materia de seguridad.
La formación general sobre concienciación en materia de seguridad debe utilizarse junto con ejercicios de phishing simulado que aborden específicamente este tipo de amenaza de phishing. Es decir, correos electrónicos que parezcan proceder de departamentos internos y que utilicen tácticas como la urgencia y amenazas de medidas disciplinarias si no se actúa en consecuencia.
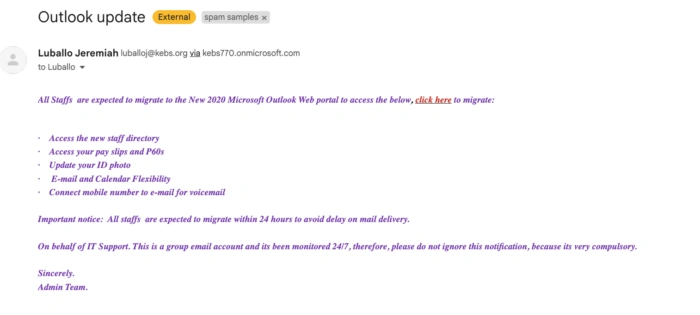
Estafas fiscales
Las estafas fiscales suelen aumentar su volumen durante la temporada de impuestos, pero pueden ocurrir en cualquier momento. A menudo, estos correos electrónicos ofrecen una devolución de impuestos. Sin embargo, el HMRC afirma explícitamente en su sitio web: "HMRC nunca enviará notificaciones por correo electrónico sobre devoluciones o reembolsos de impuestos."
Los correos electrónicos de estafas fiscales suelen tener un aspecto realista y a menudo están bien redactados. Los estafadores utilizan el logotipo de HMRC y la marca relacionada para ayudar a que los correos electrónicos de phishing parezcan legítimos. Suele haber un enlace a la página de inicio de sesión de HMRC Gateway. La página web a la que conduce el enlace es un sitio web falso que se utiliza para recopilar datos y enviarlos a los estafadores que están detrás de la estafa. A veces, estos sitios web también contienen malware, y cualquiera que navegue por ese sitio web podría acabar con un dispositivo infectado.
Cómo evitar las estafas fiscales
Las estafas fiscales pueden ser no selectivas y enviarse a cualquier persona de una organización. Sin embargo, las estafas fiscales más eficaces se enviarán a empleados específicos de los departamentos financieros. Por lo tanto, aunque es importante incluir estafas fiscales en sus ejercicios de phishing simulado para todo el mundo, también debe centrarse en educar a cualquier persona del departamento financiero sobre ellas. En vísperas de la temporada de impuestos, redoble su formación para asegurarse de que los empleados, especialmente los del departamento financiero, están preparados para el probable ataque de estos correos electrónicos de phishing.
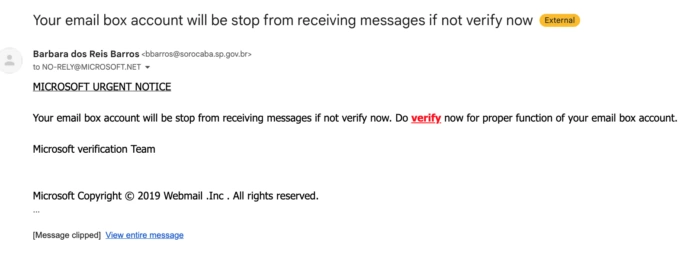
Correo electrónico de phishing: Problema con la cuenta de email
Supongamos que un empleado recibe un correo electrónico que suena urgente y le informa de que su cuenta de correo electrónico está a punto de ser suspendida o que debe ser actualizada urgentemente. En ese caso, puede sentirse obligado a hacer clic en el enlace para solucionar el "problema". Sin embargo, este correo electrónico podría ser una estafa de phishing que conduce al robo de credenciales.
El siguiente ejemplo de correo electrónico de phishing muestra cómo se ha utilizado la marca Microsoft para añadir peso a la afirmación de que la cuenta de correo electrónico del usuario está en peligro. El enlace del correo electrónico es malicioso y lleva a un sitio web que parece una página de inicio de sesión de Microsoft Office 365.
Microsoft suele figurar entre las cinco marcas más suplantadas en los mensajes de phishing. Según Cisco, las cinco principales marcas suplantadas en el primer trimestre de 2022 son:
- LinkedIn (relacionado con el 52% de todos los ataques de phishing a nivel mundial)
- DHL (14%)
- Google (7%)
- Microsoft (6%)
- FedEx (6%)
Cómo evitar el mail de phishing "Problema del correo electrónico de Microsoft"
Los estafadores suelen utilizar Microsoft y otras marcas conocidas para dar a los empleados una falsa sensación de seguridad. La lealtad a la marca y la confianza se utilizan para asegurarse de que las víctimas interactúan con el mensaje de correo electrónico y hacen clic en el enlace malicioso. Aquí es donde los ejercicios de phishing simulado pueden formar a los empleados para que desconfíen de los correos electrónicos de marca que incluyen tácticas de manipulación del comportamiento, como la urgencia.
Estafa de Google Docs
Las empresas utilizan habitualmente Google Docs para capturar documentos e ideas y colaborar con sus colegas. En 2020, Google GSuite contaba con más de 6 millones de empresas suscritas al servicio. Esta cantidad de usuarios convierte a Google en una propuesta atractiva para los estafadores.
Un reciente y novedoso uso de un ataque basado en phishing que utiliza GSuite para enganchar a un objetivo muestra lo innovadores que pueden llegar a ser los hackers. En esta estafa, un estafador crea un documento de Google y lo comenta utilizando la notación @ para dirigirse a un usuario específico. Esto hace que Google envíe una notificación por correo electrónico a la bandeja de entrada del objetivo sobre el comentario. El correo electrónico de Google es auténtico, pero contiene un comentario incrustado. Este comentario suele contener enlaces maliciosos que, si se pulsan, llevan al empleado a un sitio web malicioso.
Google ha actualizado recientemente los comentarios para que los usuarios puedan ver quién los ha dejado. Sin embargo, los estafadores actualizan constantemente sus tácticas y es posible que pronto aparezca una nueva estafa de GSuite.
Cómo evitar las estafas de GSuite Comment (y similares)
Los correos electrónicos de phishing hábilmente camuflados pueden aprovecharse de correos legítimos y servicios similares, como es el caso de la estafa de los comentarios de GSuite. Estas estafas sofisticadas dificultan que los empleados reconozcan una estafa.
La formación sobre concienciación en materia de seguridad debe reflejar las políticas de la empresa, incluido el uso de repositorios de documentos basados en la nube y quién puede y quién no puede colaborar en la documentación de la empresa. Al llevar a cabo la formación sobre seguridad, asegúrese de que dispone de la información más actualizada sobre estafas y de que el contenido refleja las estafas más recientes.
Utilice la formación sobre concienciación en materia de seguridad y una plataforma de phishing simulado que ofrezca un excelente apoyo en la creación de programas de formación basados en funciones y que ofrezcan varios idiomas y soporte de accesibilidad.
Además, es esencial reconocer que los defraudadores cambian regularmente sus tácticas para evitar ser detectados. Por lo tanto, es vital llevar a cabo una formación periódica de concienciación sobre la seguridad a lo largo del año.




