Ransomware is undoubtedly one of the biggest cyber threats affecting organisations around the world today.
Hackers have changed their tactics and rather than target everyday consumers, they are chasing the money and focusing their attention on businesses where there is a much higher return on investment.
Ransomware attacks against businesses have increased 363% within the last year, and according to Trend Micro’s security roundup report, there were over 61 million ransomware attacks detected in 2019.
The most frequently targeted industries include local governments, academic institutions, the technology sector, healthcare, manufacturing, financial services and media companies. However, every industry and business is a potential target and should be taking all the necessary steps to prevent an attack.
Unfortunately, many organisations fail to take the threat seriously enough, and it’s only when they are on the receiving end of a crippling ransomware attack that they invest the proper time and resources into improving their cyber security defences. At this stage, it’s often too late as the damage is already done.
What is Ransomware?
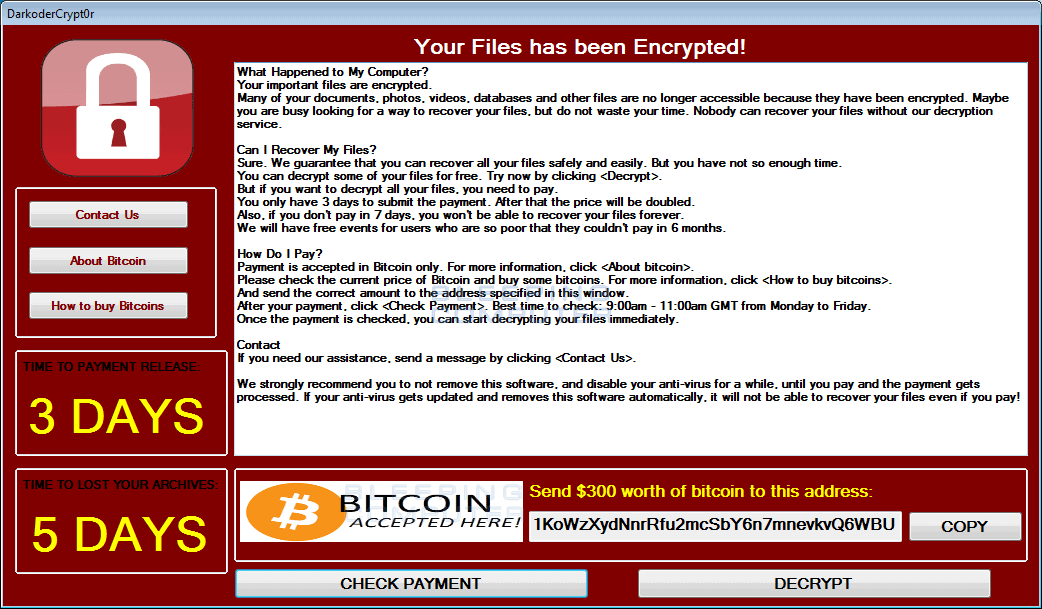
Ransomware is a type of malware that prevents users from accessing their system by encrypting files and demanding a ransom payment for the system to be unlocked. The ransom payment is usually requested in Bitcoin or in other cryptocurrencies that are difficult to trace. Cybercriminals will typically assign a deadline for the ransom to be paid, and if the deadline passes, the ransom payment will be doubled or the files permanently locked.
Certain variants of ransomware are designed to spread rapidly to other machines on a network. This is exactly what happened in the 2017 WannaCry attack when the ransomware encrypted hundreds of thousands of computers in more than 150 countries. Within a matter of hours, the ransomware wreaked havoc across the world, bringing a third of the UK’s NHS trusts to a virtual standstill.
How do you get Ransomware?
There are several ways that ransomware can infect your computer. The most common way is through phishing emails that contain malicious links or attachments. The emails will appear to come from a reputable source and once the link is clicked, or the attachment’s opened, the malware will install itself on the system and start encrypting files.
Ransomware can also be delivered via Remote Desktop Connection compromise, malicious websites, infected removable media devices and even social media messaging apps.
What to do in the event of a Ransomware Attack
1. Isolate infected machines
When ransomware strikes, speed is of the essence. If you suspect that your computer has been infected, you should immediately disconnect it from the network by unplugging the ethernet cable and disabling Wi-Fi, Bluetooth, and any other networking capabilities. Ransomware spreads via your network connection so if you can isolate the infected machine, it will prevent it from spreading and infecting other devices on the network. If you suspect that more than one machine has been compromised, apply the same measures.
2. Notify your IT security team
Your IT team should immediately be notified so they can contain the spread of the ransomware and put in place the correct procedures to deal with the attack. This is where an incident response plan comes into play. The plan will help ensure that the incident is properly managed, all evidence is gathered, recorded and maintained, and that the situation is dealt with as quickly and efficiently as possible. Providing a detailed timeline of the breach will help identify any weaknesses in procedures and improve security defences going forward.
3. Identify the type of ransomware
If you’re able to identify the type of ransomware that is being used in the attack, it will help you understand how it spreads, what types of files it encrypts and how it can be removed. There are lots of different strains of ransomware but the two most common are screen locking ransomware and encrypting ransomware. The first is the easiest to resolve and despite locking down the entire system, files will be safe until a ransom payment is made. The second is much more difficult to recover from. Instead of denying the user access, it finds all the sensitive data, encrypts it, then demands a payment in order for the data to be decrypted and restored.
4. Inform employees
You should immediately inform your employees that there has been a breach, explain what it means for the company and outline what steps you will be taking to mitigate the incident. Whether or not their computers have been directly infected, there is likely to be some operational downtown as investigations into the incident take place. Employees will naturally worry about the impact the attack will have on their job so it’s important to be transparent and keep them fully briefed on the evolving situation.
5. Change login credentials
Ransomware can spread rapidly by gathering IP addresses and credentials. If hackers manage to compromise administrative credentials they can move laterally around networks, encrypt files and wipe out backups in the process. To ensure your system is secured and to prevent hackers from thwarting your recovery efforts, you should immediately change all admin and user credentials.
6. Take a photo of the ransom note
If possible, you should take a photo of the ransom note on your mobile phone. This can be used as evidence when you are reporting the incident to the police. This evidence is necessary if you are filing a cyber insurance claim and the photo may also provide further information on the attack method.
7. Notify the authorities
It’s important to notify the police if you’ve been attacked so they can fully investigate the incident and help prevent other companies from suffering the same fate. If your organisation handles data that belongs to citizens within the EU, you are legally bound under the GDPR to inform the ICO within 72 hours of a breach taking place. Failure to do so could result in fines of up to 4% of annual global turnover or 20 million euros (whichever is greater).
8. Never pay the ransom

The National Crime Agency strongly advises organisations not to make a ransom payment as it emboldens cybercriminals to launch further attacks and the vicious cycle continues. If you choose to make a ransom payment, there is no guarantee you will ever get your files back, and if anything, it increases your chances of being targeted again in the future.
9. Update security systems
After the incident is over, you’ll need to perform a security audit and update all systems. Updates should be installed as soon as they become available to prevent hackers from exploiting vulnerabilities in older versions of the software. Regular patching will ensure that machines are kept up to date, stable, and safe from malware.
10. Recover from backups
The key to a quick recovery from a ransomware attack is to ensure you have up to date backups of important files. The 3-2-1 rule is a best practice approach for backup and recovery. Following this rule, you should have 3 copies of your data in two different storage formats – with at least one copy located offsite. This will enable you to recover your data quickly without being blackmailed into making a ransom payment.
How to Prevent Ransomware Attacks
- Employees should receive regular cyber security awareness training to educate them about evolving cyber threats and how to spot the early stages of an attack.
- Backup data on a regular basis.
- Restrict users’ permissions to install and run software applications. This may limit the malware’s capability to spread throughout a network.
- Regularly update software and ensure patches are installed as soon as they become available.
- Install anti-virus software on all devices.
- Scan all incoming and outgoing emails to detect threats.
- Follow good security practices to minimise the risk of infection – Avoid clicking on links or downloading attachments from unknown sources.
- Configure firewalls to block access to malicious IP addresses.
- Create strong passwords and enable multi-factor authentication for extra security on accounts.
Phishing is the number one cause of all cyber attacks and continues to prove one of the easiest ways to steal valuable data and deliver ransomware. MetaCompliance’s phishing simulation software MetaPhish has been created to provide a powerful defence against these threats and enables organisations to find out just how susceptible their company is to phishing. Get in touch for further information on how MetaPhish can be used to protect your business.







