Ransomware is an advanced form of cyber attack, and one of the biggest cyber threats facing organisations across the world today.
Since the start of the pandemic, there has been a global surge in attacks. Through the first half of 2021, 304.7 million ransomware attacks have been recorded wordwide, surpassing 2020’s full-year total (304.6 million).
Ransomware has hit manufacturing companies the hardest, accounting for nearly 25% of all attacks, followed by professional services at 17%, and government organisations at 13%. Schools and universities have also been hit hard due to the move to virtual or hybrid classes during Covid-19.
The chaos and disruption caused by the outbreak have created the perfect environment for these types of attacks to flourish, and Covid-19 themed phishing lures have proved a very successful way to deliver malicious links.
Many organisations fail to take ransomware seriously, and it’s only when they are on the receiving end of a crippling attack that they invest the proper time and resources into improving cyber security defences. However, at this stage, it’s often too late as the damage is already done.
What is Ransomware?
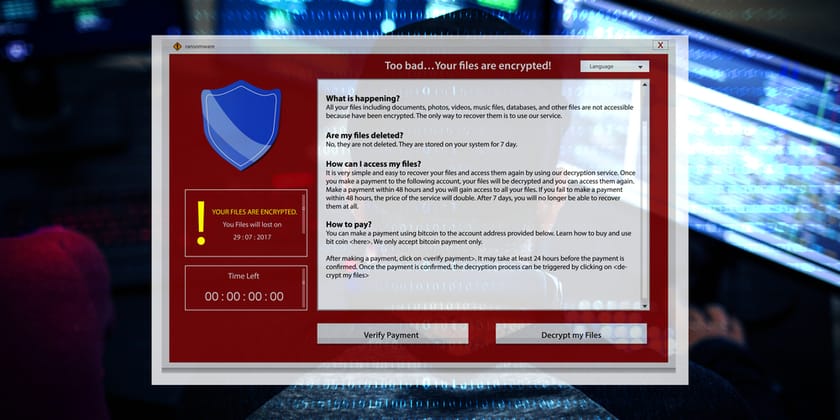
Ransomware is a type of malware that prevents users from accessing their system by encrypting files and demanding a ransom payment for the system to be unlocked. The ransom payment is usually requested in Bitcoin or in other cryptocurrencies that are difficult to trace. Cybercriminals will typically assign a deadline for the ransom to be paid, and if the deadline passes, the ransom payment will be doubled, or the files permanently locked.
Certain variants of ransomware are designed to spread rapidly to other machines on a network. This is exactly what happened in the 2017 WannaCry attack when the ransomware encrypted hundreds of thousands of computers in more than 150 countries. Within a matter of hours, the ransomware wreaked havoc across the world, bringing a third of the UK’s NHS trusts to a virtual standstill.
Within the last year, the ransomware strain that has been seen most frequently is Sodinokibi (also known as REvil). This Ransomware-as-a-Service (RaaS) attack model first emerged in 2019, but it has rapidly evolved by capitalising on blended ransomware and extortion attacks. It’s proved to be an extremely lucrative attack model, with developers claiming to have made over $100 million in the past year alone.
How is Ransomware Deployed?

There are several ways that ransomware can infect your computer. The most common way is through phishing emails that contain malicious links or attachments. The emails will appear to come from a reputable source and once the link is clicked, or the attachment’s opened, the malware will install itself on the system and start encrypting files.
Ransomware can also be delivered via malicious websites, infected removable media devices, social media messaging apps, and in some cases, attackers have gained access to networks by using brute force attack on a vulnerable network device.
5 Ways to Protect your Organisation from Ransomware Attacks
1. Keep Software and Operating Systems Updated
Hackers will frequently exploit vulnerabilities in operating systems and common applications to deploy ransomware. Network vendors regularly release patches to address security vulnerabilities so it’s vital you apply these as soon as they become available. Patching is estimated to prevent up to 85% of all cyber attacks by keeping systems up to date, stable, and safe from malware and other threats.
2. Intrusion Prevention and Detection Technologies
Intrusion detection technologies can give a detailed insight into the traffic on your network. They will provide a real-time view of your network and identify any anomalies that could suggest your organisation is being breached. If any suspicious behaviour is detected, you will be alerted immediately, enabling faster threat detection and response.
3. Backup Data
Backups must be conducted regularly so that minimal data is lost in the event of a ransomware attack. The 3-2-1 rule is a best practice approach for backup and recovery. Following this rule, you should have 3 copies of your data in two different storage formats, with at least one copy located offsite. Backups should be tested regularly to make sure they are working as expected. In the event of an attack, this will enable you to recover your data quickly without being blackmailed into making a ransom payment.
4. Enable Multi-Factor Authentication
Cybercriminals will frequently use stolen employee credentials to gain entry into networks and deploy ransomware. The credentials are often obtained from phishing attacks or harvested from one of the many data breaches. Enabling multi-factor authentication will mean that even if hackers have a user’s credentials, they won’t be able to gain access to the network without another authenticating factor such as a pin, code, token, or biometric data.
5. Cyber Security Awareness Training
Ransomware attacks rely heavily on a user opening a phishing email. To ensure that employees can effectively recognise these threats, it’s vital they receive regular cyber security awareness training. The training should be multi-layered and incorporate phishing simulation tests to train staff on what phishing emails look like and how they can avoid them. Regular phishing tests will help increase awareness and identify vulnerable staff members that require additional training.








