O que são as "Hash Functions"? As funções de hash desempenham um papel crucial na segurança das palavras-passe para serviços Web seguros. Estes serviços nunca armazenam a sua palavra-passe real, mas sim uma versão com hash da mesma. As funções de hash são algoritmos que convertem dados de entrada (como uma palavra-passe) numa cadeia de caracteres de tamanho fixo. Este processo é irreversível, o que significa que é quase impossível obter a entrada original a partir do hash. Quando o utilizador inicia sessão, o serviço faz o hash da palavra-passe fornecida e compara-a com o hash armazenado. Desta forma, mesmo que ocorra uma violação de dados, os hackers não conseguem aceder a palavras-passe em texto simples, aumentando a segurança geral.
Um procedimento de início de sessão pouco sofisticado
Vejamos primeiro o aspeto de um procedimento de início de sessão não sofisticado. Iniciamos sessão num serviço Web da forma habitual, com um nome de conta e uma palavra-passe:
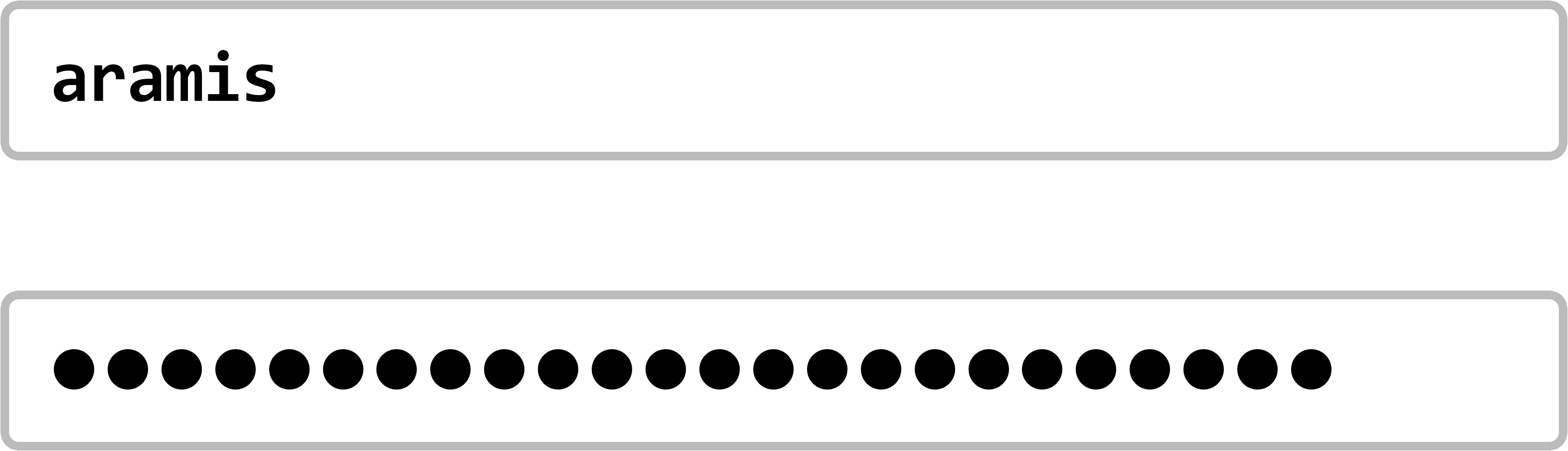
O nosso serviço Web pouco sofisticado tem uma tabela na sua base de dados com todos os nomes de contas e as respectivas palavras-passe:

O serviço Web começa por procurar na sua base de dados o nome da conta a partir do formulário de início de sessão preenchido. Se o nome existir na base de dados, o serviço também compara a palavra-passe do formulário de início de sessão com a palavra-passe associada na base de dados. Se as palavras-passe coincidirem, o registo é efectuado. Caso contrário, o registo é recusado. À primeira vista, este é um procedimento de início de sessão seguro. Apenas aqueles que possuem um nome de conta válido e sabem a palavra-passe associada podem aceder à conta correspondente. Todos os outros são recusados. Até aqui, tudo bem! Mas o que há exatamente de pouco sofisticado neste procedimento?
O problema é que as palavras-passe são armazenadas numa base de dados. Isto significa que são potencialmente conhecidas por todos os que têm acesso à base de dados, incluindo os operadores de serviços Web e os seus empregados. Além disso, é agora prática comum para muitas empresas subcontratar a operação efectiva dos serviços Web que oferecem a fornecedores de computação em nuvem dos EUA, como a Amazon Web Services ou a Google Cloud. Por conseguinte, podemos assumir que, em princípio, os operadores e funcionários destes fornecedores de computação em nuvem também têm acesso à base de dados e, consequentemente, à nossa palavra-passe. Além disso, é claro que os criminosos também podem obter acesso não autorizado aos dados da base de dados.
Além disso, não é segredo que a maioria dos utilizadores de serviços Web reutiliza a mesma palavra-passe para vários serviços. Assim, quem quer que tenha conseguido obter a palavra-passe para a conta Facebook/Twitter ou para a agência de viagens em linha de um alvo terá, com um pouco de sorte, também a palavra-passe para o seu correio eletrónico, banco em linha, organizador pessoal, uma plataforma de encontros e a intranet da empresa onde o alvo trabalha. O incentivo económico para roubar palavras-passe da base de dados de qualquer serviço Web é correspondentemente elevado, mesmo que esse serviço Web não seja um alvo lucrativo! A questão é: como é que resolvemos este problema?
Um procedimento de início de sessão mais sofisticado
Recordemos: O serviço Web descrito acima tem uma tabela na sua base de dados com todos os nomes de contas e as respectivas palavras-passe:

Adaptamos esta tabela da seguinte forma. Em vez de armazenar as palavras-passe, aplicamos uma função criptográfica de hash à nossa escolha às palavras-passe:
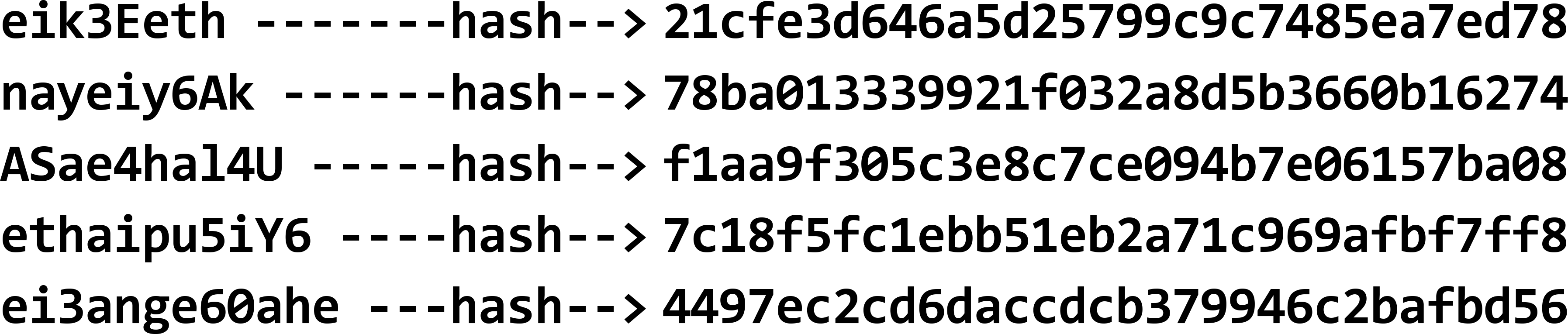
Depois, em vez das palavras-passe, armazenamos os valores hash resultantes na base de dados:

Isto altera apenas ligeiramente o procedimento de início de sessão. Continuamos a iniciar sessão da forma habitual, com um nome de conta e uma palavra-passe:

O serviço Web procura primeiro o nome da conta a partir do formulário de início de sessão preenchido na sua base de dados. Mas no passo seguinte, o novo procedimento é diferente. Se o nome existir na base de dados, a função hash é aplicada à palavra-passe do ecrã de início de sessão. Só então o valor hash resultante é comparado com o valor hash correspondente na base de dados. Mais uma vez, as palavras-passe já não são comparadas entre si, mas apenas os seus valores de hash. Se os valores de hash coincidirem, o início de sessão é efectuado. Caso contrário, o login é negado.
Para além da utilização da função hash, nada mudou no procedimento de login. A partir das propriedades das funções de hash criptográficas, conclui-se que comparar os valores de hash é tão bom como comparar diretamente as palavras-passe. Mas agora, as próprias palavras-passe já não são armazenadas na base de dados do serviço Web. Qualquer pessoa que tenha acesso à base de dados - autorizada ou não autorizada - já não tem acesso às palavras-passe, mas apenas aos seus valores de hash. O incentivo económico acima descrito para roubar as palavras-passe da base de dados de um serviço Web é assim eliminado porque as palavras-passe já não estão contidas na base de dados.
Como funcionam as funções hash na prática
Esperamos ter conseguido explicar melhor como é possível e porque é prática comum que os serviços Web seguros nem sequer conheçam as palavras-passe que utilizamos para iniciar sessão. Na prática, a segurança deste procedimento é aumentada gerando os valores de hash com uma função de hash criptográfica especializada(bcrypt) e associando-os adicionalmente a uma cadeia de caracteres secretos (salt) em toda a base de dados antes de aplicar esta função de hash.
Se se esqueceu da sua palavra-passe para um serviço Web, pode solicitar uma redefinição da palavra-passe à maioria dos serviços Web. Receberá um e-mail com uma ligação que o levará a um formulário onde poderá definir uma nova palavra-passe. Sabemos agora porque é que isto é tratado de forma tão estranha: o serviço Web não sabe a sua palavra-passe antiga. Infelizmente, nem todas as empresas seguem esta prática de segurança estabelecida. Se indicar por correio eletrónico ou numa chamada telefónica com uma equipa de apoio que se esqueceu da sua palavra-passe e depois lhe for efetivamente indicada a sua palavra-passe, pode concluir que essa empresa não cumpre as normas modernas de segurança da informação. Assim, o mais tardar, deve certificar-se de que não utiliza esta palavra-passe em qualquer outro contexto. Para utilizar consistentemente uma palavra-passe separada para cada serviço Web, deve utilizar um gestor de palavras-passe. Assim, já não precisa de se lembrar de muitas palavras-passe individuais e tem o bónus adicional de poder criar palavras-passe aleatórias de alta qualidade. Existem plug-ins de browser para gestores de palavras-passe populares que até preenchem os ecrãs de início de sessão dos seus serviços Web por si. Raramente a conveniência e a segurança se encontram de forma tão perfeita.
Integrar a segurança das palavras-passe e as funções de hash na sua formação pessoal em cibersegurança
Em conclusão, as funções hash desempenham um papel crucial para manter as palavras-passe a salvo de ataques informáticos. No entanto, a sua eficácia depende muito da forma como as pessoas compreendem e gerem as suas palavras-passe. É aqui que entra a formação em cibersegurança. Ao ensinar as pessoas a criarem palavras-passe fortes e a estarem atentas às ameaças em linha, todos nós podemos contribuir para manter as nossas informações pessoais seguras. Lembre-se, manter-se seguro em linha é um esforço de equipa, e um pouco de conhecimento ajuda muito a protegermo-nos no mundo digital.