Discover how effective security incident reporting helps prevent incidents from escalating into breaches, enhancing organisational safety and compliance. Reducing the harm caused by a cyber security attack starts by recognising an incident has happened. Being aware of imminent danger makes an organisation resilient to the impacts of cyber security. These impacts are not to be ignored; estimated costs from security breaches to global business are expected to reach $10.5 trillion (£7.7 trillion) in the coming few years.
Mitigation of security breaches begins with an awareness of a security incident. In practical terms, security incidents need to be recorded and this is the job of an incident reporting system that gives a team the information needed to deal with a security event.
Types of Security Incidents to Report
The problem with cyber security is that it is often hidden in plain sight. An IBM survey found that it takes, on average, 287 days to detect and contain a data breach. The same IBM report found that organisations that respond quickly to an incident saved 30% in costs and reduced the time to contain a threat to under 200 days. But when you begin to set up an incident reporting process, what types of security threats should you expect to capture in the incident report?
The UK’s Information Commissioner’s Office (ICO) carry out a trend analysis each year that shows the type of security incidents that end up on their desk:
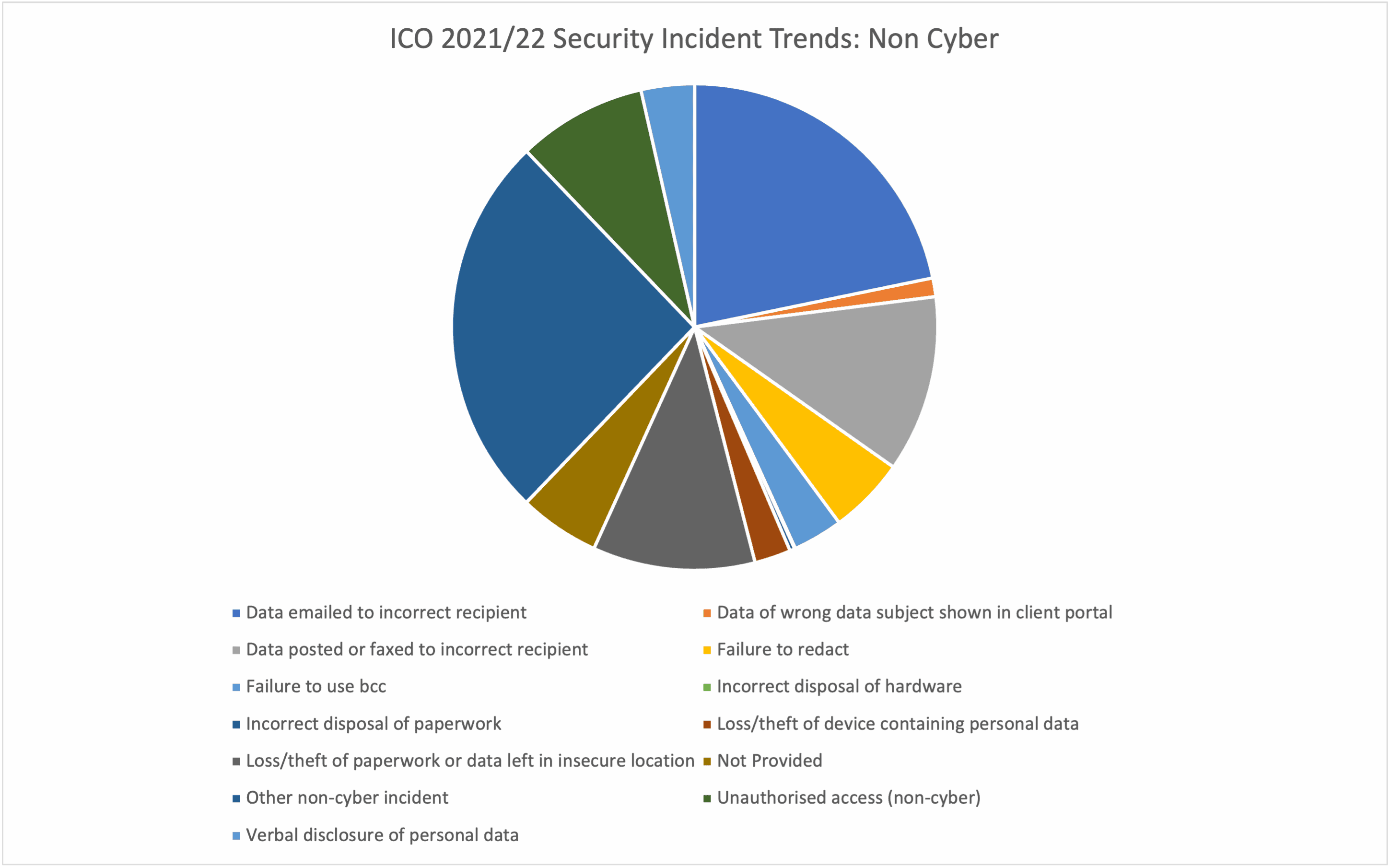
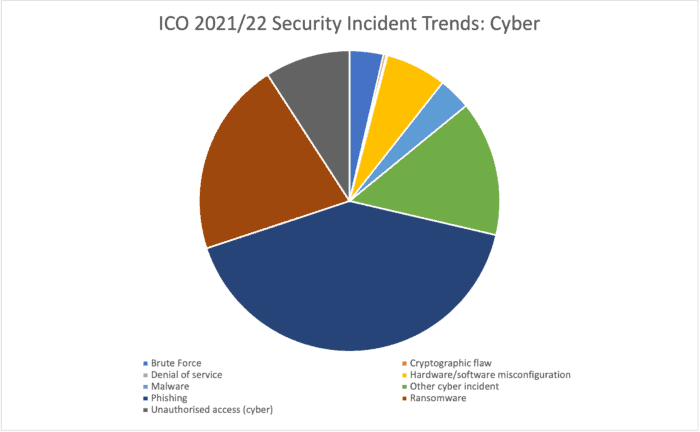
Source: UK ICO
Using industry intelligence helps to determine the types of security incidents that need attention:
Phishing
The human operator is where many cyber attackers focus attention. Phishing is the most common method that fraudsters use to trick an employee into providing login credentials and other personal data. A security incident reporting system should be able to easily capture the details of a suspected phishing message. The incident report should contain details of any interaction with the message, especially if a link in an email/message has been clicked. Further details of what happened next should be captured to indicate the extent of the incident.
Read Phishing Prevention Strategies: Safeguarding Your Organisation’s Data to learn more about how to protect your organisation from phishing attacks. Explore strategies that can help safeguard your company’s sensitive data and reduce the risk of successful cyber attacks.
Lost Device
Company devices can contain a lot of sensitive information. As well as company devices, remote work increased the use of personal devices for corporate cloud app access. A lost or stolen device can end up in the wrong hands resulting in data exposure as increasingly companies use data syncing with cloud apps. If a phone used for company work has been lost or stolen, the incident should be quickly recorded so that triage on the incident can be carried out and an appropriate response initiated.
Accidental Data Leak
Research has found that 58% of employees have sent an email to the wrong person. Misdirection or mis-delivery of an email can result in data loss and non-compliance with data protection regulations. Incident trends from the UK’s ICO show that email-related data exposure is the biggest contributor to security incidents. If an employee believes they have sent out an email containing sensitive information to the wrong person(s) then this should be reported.
Other Email-Related Incidents
One of the biggest issues in accidental data exposure is simply forgetting to bcc a list of recipients into an email exchange. As soon as the employee realises they have forgotten to bcc recipients, they should report the incident so that triage can be started and the event handled in line with company policy.
5 Reasons to Report Cyber Security Incidents
There are sound reasons to set up a robust incident reporting process. The results are beneficial to both company and employee and include:
Incident Reporting Encourages a Culture of Security
The ethos underlying a culture of security is about being “all in this together”. Incident reporting should not be a fearful thing, but part of an everyday process. Make incident reporting part of the company norm and expected employee behaviour when something worrying happens. By providing an easy and fast way to report incidents, employees become part of the push back against cyber attacks. This helps to foster a community spirit in tackling cybercrime and fraud.
Develops a Streamlined Process to Prevent Incidents from Becoming a Serious Attack
The reporting infrastructure must be based on an incident reporting framework, configured to fit your organisation’s needs, and utilising automated workflows. An incident reporting system should be configurable to allow escalation through reporting to triage to mitigation, whilst ensuring the most appropriate person is alerted once the process of security incident reporting begins.
Enforces Security Policies
Having a security incident process in place helps to enforce your company’s security policy. A reporting system that uses incident workflows provides a framework to take an incident through triage to mitigation based on security policy advisories.
Prevents Costly Security Events
An incident that becomes an event such as a data breach, results in financial and other costs. IBM’s “Cost of a Data Breach Report” has seen 2021 take the accolade of the highest data breach costs in 17 years. By developing a reporting culture in your organisation and making reporting incidents easy, your team is more able to prevent an incident from becoming a full-blown security event.
Helps to Maintain Regulatory Compliance
Maintaining a record of compliance is a default in many regulations and standards including ISO27001, DPA2018, and GDPR. These records also extend to the various breach notification requirements of data protection regulations. Incident reporting allows an organisation to prove that they take security seriously and demonstrate mitigative actions taken. A reporting system should allow an organisation to take the details of a suspected breach and then output these to generate a report if a breach notification is required.
Read Transform Compliance Management into a Competitive Advantage to explore how robust compliance practices can not only ensure security but also give your organisation a competitive edge in today’s market.
Three Best Practices for Security Incident Reporting
The use of incident reporting for health and safety reasons is well established. By collating H&S data, companies can help ensure a safe working environment and meet regulatory expectations. Security incident reporting is an extension of this health and safety culture that provides a framework to deal with an imminent threat. However, reporting requires that certain baseline best practises are followed:
1) Easy Security Incident Reporting
An incident reporting system should be easy to use by all. Entry of incidents should guide an employee, capturing the most important details that are needed to begin the escalation process. Barriers to entry, such as complicated forms, etc., should be avoided.
2) Appropriate Escalation
The incident reporting system should be configurable to allow an administrator to create workflows that reflect the structure of the team dealing with security incidents. By using an automated workflow that sends out appropriate and tailored alerts to the right people, data breaches and other security events can be prevented.
3) Audit and Report
An incident reporting system must be able to audit incidents and actions and generate reports. These reports can then be used as evidential documentation to prove compliance with regulations and standards. The incident report also forms a baseline of evidence for a data breach notification report, if required.
Incident reporting is important to prevent a security incident from becoming a security breach. But the system that collects the incident details must be able to work to best practises. Collection of data is where the escalation begins, and this must allow easy input of data, yet collect enough information to be informative. Automated workflows provide the backbone for effective escalation and make the incident reporting process seamless.








